Cybersecurity services that defend your data
Improve your cybersecurity posture and reduce risk with comprehensive services provided by highly certified experts.
Organizations struggle to achieve and maintain their desired security posture due to limited resources, competing priorities, and a lack of expertise in their internal teams. Flexential Professional Services helps you advance your cybersecurity program with a prioritized approach that reduces risk, increases defense-in-depth, and empowers your IT security team.
- Increased sophistication and complexity of cyber-attacks threaten critical data, operations, customers, and business operations
- Lack of understanding of the current risk profile, including which risks are most critical, and what remediation actions are most urgent
- Internal teams with gaps in knowledge or experience, and insufficient time and resources to stay ahead of bad actors
- Lack of a programmatic approach to advance cybersecurity maturity and defense-in-depth against new threats from supply chain attacks, AI, and ransomware extortion
Assess security posture and discover weaknesses. Receive a risk-based plan to strengthen defenses, close gaps, and remediate vulnerabilities.
Assess risks for personally identifiable information (PII) and sensitive business data, such as protected health information (PHI) or credit card data. Receive actionable, prioritized, and detailed mitigation guidance.
Develop, implement, and mature a robust cybersecurity program that programmatically applies risk and cybersecurity best practices to increase defense-in-depth by improving defense and detection capabilities, strengthening response capabilities, and managing IT risks. Our certified experts systematically guide your team through processes and best practices tailored to your organization and requirements.
Ethical hacking and social engineering uncover cyber defense weaknesses. Receive actionable and prioritized findings with detailed countermeasure guidance to mitigate risk, strengthen defenses, and increase cyber resiliency.
Expose and remediate cyber defense weaknesses today
Preparedness assessment and incident response plan analysis to create comprehensive and detailed incident response plans, including tabletop exercises.










Explore additional products and services
Explore these additional services for your organization. Schedule a consultation with our expert team and learn how you can benefit from Flexential Professional Services.
Disaster Recovery as a Service
Minimize unplanned downtime with cost-effective DRaaS, low RTOs and RPOs, and comprehensive DR planning and testing. Built for cloud, on-premises, and hybrid environments.
Professional Services for Disaster Recovery
Protect your operations against disruptions, minimize data loss, and maintain availability with a tailored and tested DR plan from experienced consultants.
Backup as a Service
Protect data with offsite backups and stringent security that support full data recovery and restores in the event of an incident.
Architecture and Transformation
Our teams follow proven methodologies to define a clear future state and architect, transform, and modernize IT environments.
Compliance Management
Complex compliance requirements? Achieve compliance, reduce risk, and increase security with our highly certified compliance team.
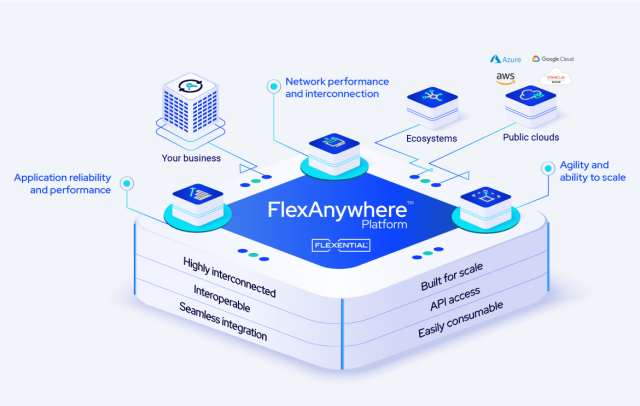
FlexAnywhere®: Hybrid IT flexibility without compromise
Flexential's highly connected FlexAnywhere® platform delivers tailored infrastructure with automation, a pay-as-you-go-and-grow model, and scalability for your business needs.
RELATED RESOURCES
Explore more professional services resources
Accelerate your hybrid IT journey, reduce spend, and gain a trusted partner
Reach out with a question, business challenge, or infrastructure goal. We’ll provide a customized FlexAnywhere® solution blueprint.