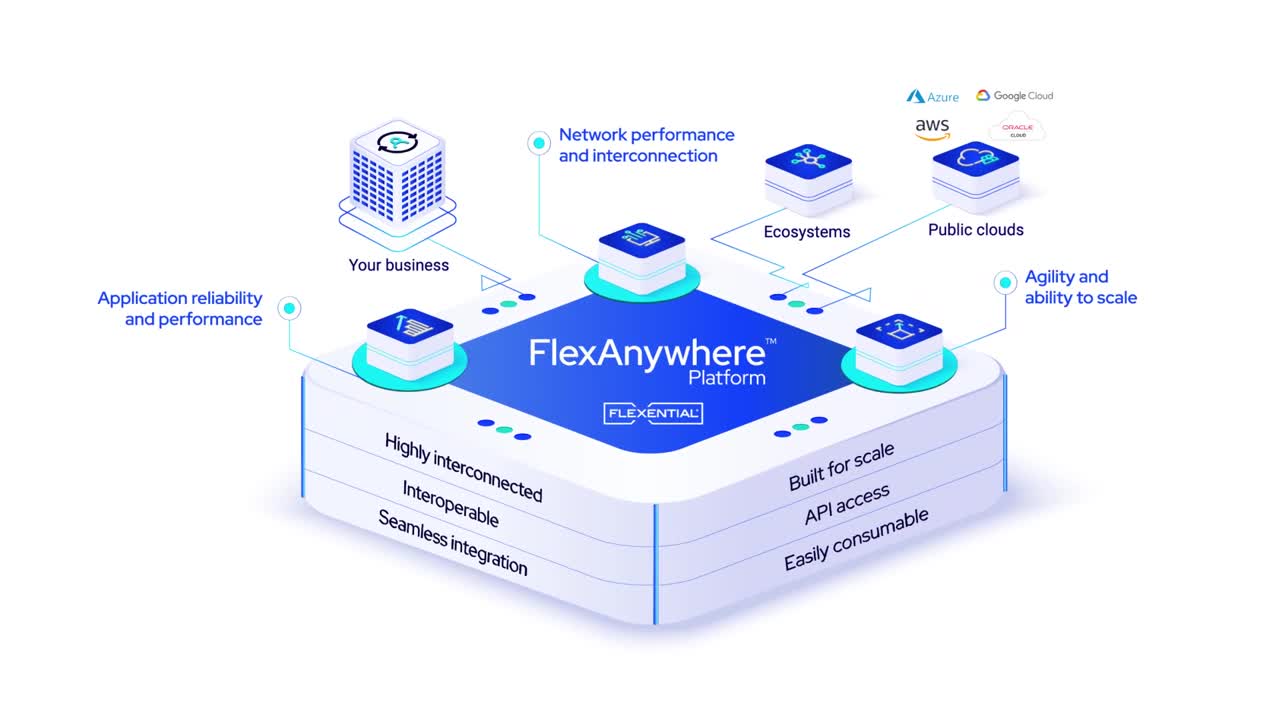
What new high-density workloads could you support with 48% ROI?
FlexAnywhere® Solutions give customers the tools to solve hybrid IT challenges, support AI and machine learning initiatives, and seamlessly interconnect applications.
- Meet new strategic initiatives and changing market conditions as workloads grow more distributed.
- Quickly scale resources, infrastructure, and data center footprint up or down according to demand and forecasts.
- Future-proof aging infrastructures alongside new deployments that offer industry-best time to revenue.

- Improve network response time, high-density distributed workloads, and user experience.
- Handle compute-heavy AI and machine learning initiatives that fuel business growth.
- Improve reliability to hyperscalers for stronger performance and reduced single points of failure.

- Ensure even the most compute-intensive apps are available with near-zero RTOs/RPOs with sustainable liquid-ready cooling systems.
- Drive business growth with industry-leading SLAs and buyer-friendly leases on contiguous space.
- Experience industry-leading network availability that delivers the confidence of no interruptions.

Every client is unique—their existing architecture, pain points, and plans for high-capacity workload expansion. The FlexAnywhere® Platform is tailored to meet those needs—today and tomorrow.
“[Flexential] adds a ton more value than just what a monthly bill shows. Sometimes a partnership is worth its weight in gold on an invoice, and that’s what we have here.”
–SVP of Technology & Innovation, Automotive Software
From a single rack to multi-megawatt—scalable, tailored data center facility solutions for your unique IT infrastructure.

Unlock enterprise-grade colocation without the upfront costs.
Reliable and secure interconnection built to handle AI- and machine-led business growth.
Accelerate your cloud on-ramp while reducing cost.
Public, private, and hybrid options that scale with new strategic initiatives.

Maximize your cloud infrastructure investments with data-driven recommendations tailored to you, in a no-cost, no-obligation workshop.
Keep your business always-on with reliable planning, disaster recovery, and backup solutions.

Implement an end-to-end DR program with expert guidance for reliable and trusted disaster recovery
End-to-end tailored engagements that solve your most complex transformation, security, and compliance challenges.

Partner with our infrastructure experts in a dedicated network transformation workshop.

“Our clients rely on us to deliver high-performing, reliable IT environments so their healthcare data and applications are secure and always available. Flexential is key in helping us deliver this essential service.”